Hackers breached MSPs and use Webroot SecureAnywhere tools to infect customer PCs with the Sodinokibi ransomware. Hackers used MSP’s remote desktop took by Webroot to gain access to customer’s PCs and infected PCs. They executed a powershell script on remote workstations to publish the Sodinokibi ransomware applet. Topics: Insider azim pemji…
In network security planning, it’s important to find the biggest network security issues that can be fixed with the least amount of time and effort. Fixing major security flaws in your network helps to prevent cyberbreaches by closing potential avenues of attack. The question is: “What are the biggest network security…
In Warren Buffett’s 2019 shareholder letter, he called out the “Big One” alongside natural disasters as the key risks to his insurance portfolio. The “Big One” he is referring to is a cyber attack he describes as “…having disastrous consequences beyond anything insurers now contemplate.” Here’s a CEO cheat sheet to…
Baltimore still isn’t able to provide basic city services two weeks after a powerful ransomware attack. And a full recovery may take months, Mayor Bernard C. “Jack” Young says. The damage includes police surveillance cameras that are shut down and utilities payment systems that were forced offline. Broad phone and email…
Data breaches have become so common these days that they’re hardly news anymore—unless they’re truly massive breaches like the Yahoo cyberbreach that affected 3 billion users. With cyber threats constantly emerging and evolving as time goes on, it’s not a question of if your company will suffer a network security breach, but when. Do you…
The coronavirus (COVID-19) outbreak has changed the way that many people work. With the forced closure of offices throughout the country, many employees who had never been on remote work programs before had to work from home for the very first time. While being able to work from home has…
A new research from cybersecurity firm Kaspersky Lab revealed that the number of Distributed Denial of Service (DDoS) attacks increased by 84 percent in the first quarter of 2019 compared to Q4 of 2018. In its research report dubbed DDoS Attacks in Q1 2019, Kaspersky stated that cybercriminals are once again…
Another data leak in Facebook’s timeline. This time it’s the Facebook-owned photo-sharing application Instagram. An unprotected AWS (Amazon Web Services) server containing personal information of millions of Instagram influencers, celebrities, and brand accounts have been found online, the TechCrunch reported. According to the security researcher Anurag Sen, who discovered the leak and…
Discover the common challenges faced in protecting data in the cybersecurity landscape and the strategies to overcome them. Understanding the Importance of Data Protection in Cybersecurity Data protection is a critical aspect of cybersecurity. In today’s digital age, organizations collect and store vast amounts of sensitive data, including personal information,…
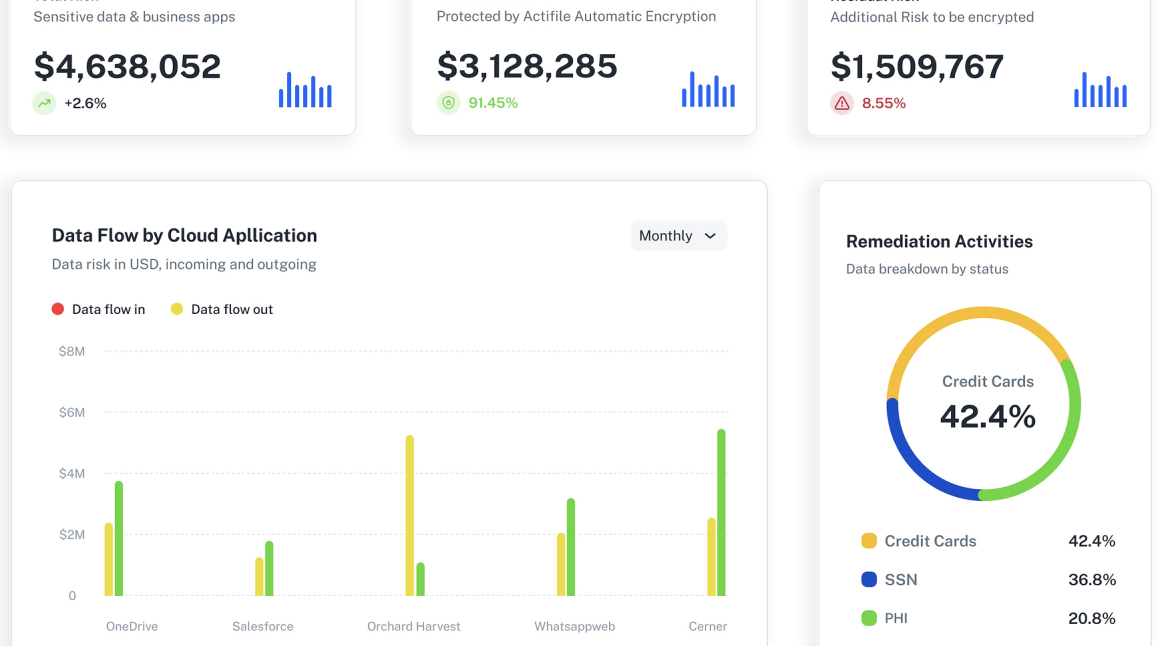
Unveiling the Power of Quantifying Cyber Risk: A Journey with ideaBOX In the realm of cyber risk, ignorance is not bliss. While many business leaders may unknowingly adopt a “what we don’t know can’t hurt us” mentality, understanding and managing cyber risks are paramount in today’s digital landscape. In a…